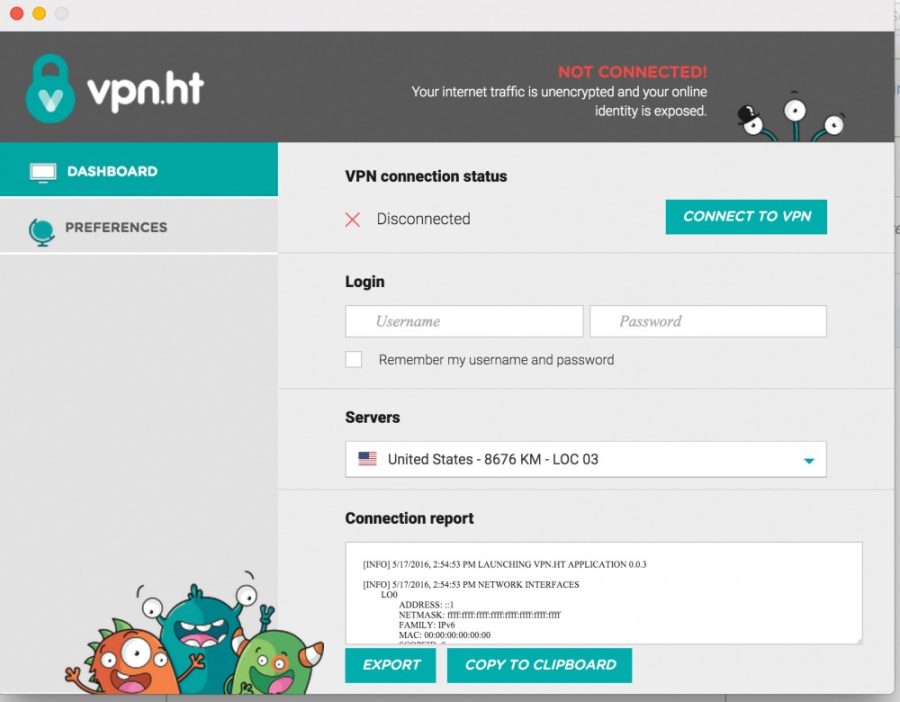
Connecting. Encrypted. Secured. You’re in. You can now freely and securely browse the web. Though this seems like something out of a ‘90s hacker movie, what’s actually being described is the process of connecting to a virtual private server (VPN).
A VPN is a secure connection through an encrypted tunnel to a remote server — a mouthful of a description. At a technical level, the way a VPN works is quite complex, but the way to describe it is rather simple. Instead of directly connecting to websites through your browser, your traffic is first encrypted and sent to the VPN server you’re using. Then you access the internet from behind this server, effectively hiding your IP address — a kind of internet fingerprint — from the sites you’re accessing, along with preventing your information from being intercepted on the local network you’re using, such as a library’s internet.
While your traffic being intercepted sounds like tinfoil-hat-wearing paranoia, in reality it’s rather easy to spy on someone’s web traffic. Intercepting traffic is especially easy if the WiFi you’re using is a public network, such as from a coffee shop. When using a public Wi-Fi network there is almost no guarantee of the safety of your web data. The security of your data depends entirely on the safeguards put in place by whomever is hosting the public network. If that local coffee shop you enjoy doesn’t seem like they have a bunch of money to throw into making their internet as secure as possible, it probably isn’t.
RELATED: Campus Guide ’17: Net Neutrality should be appreciated, defended
When you use a VPN, this traffic instantly becomes encrypted so even if it’s intercepted, its contents can’t be read without knowing how to decrypt it. This prevents fellow patrons and the business from watching how you use the web.
There are countless companies and organizations that offer VPN services. Some are provided for free, but more often than not they require a paid subscription at a relatively low cost. I strongly feel these paid subscriptions are worth the cost, especially if the VPN service is providing a high level of security and anonymity. One such service is NordVPN, a privacy-centered VPN service based in Norway.
Another major benefit of using a VPN is avoiding censorship. If your internet service provider or government is censoring internet content, you can connect to a VPN server located somewhere like Panama to subvert this censorship. This makes VPNs a critical tool for keeping the internet free, open and uncensored.
While generally I don’t advocate circumventing the internet blocks at your place of work, a VPN can be useful in bypassing these restrictions. More often than not, these blocks are put into place to prevent access to explicit content. But it can be frustrating when you’re trying to fix some problem with your phone and the most promising Google result gets blocked for containing content related to “hacking.” A VPN is a quick solution to such a problem.
Some institutions, such as Pima Community College, even block access to sites related to VPNs. How’s that for irony?
There are many types of VPNs and each uses a different system, and each requires different steps to set up. Most VPN services utilize an open-source utility called OpenVPN. This provides for a simple way to universally use one VPN service across all of your devices. But all of this information is useless if you can’t set one up on your personal computer or phone.
RELATED: Scarier than needles: Expert talks medical device hacking
Usually, whichever VPN service you are using offers resources and guides for connecting to their specific service. These guides are dependent on which sort of VPN the service utilizes and what sort of internet device the service is being set up on. However, the process is predominantly universal with only slight differences between each device, whether it be an iPhone or a Windows computer. The service equips you with a username and password along with a server address, which you put into either a VPN tool or your internet settings. From there, it’s as simple as clicking a button to securely browse the web.
While VPNs aren’t completely foolproof and secure, they give you an added layer of security. Each layer of security makes it that much harder for someone with malicious intent to steal your personal information or spy on your web usage. This makes it more likely an attacker will give up on you and move on to an easier target. As the old adage goes, locks only keep honest people honest.
Follow Brian Winkler on Twitter